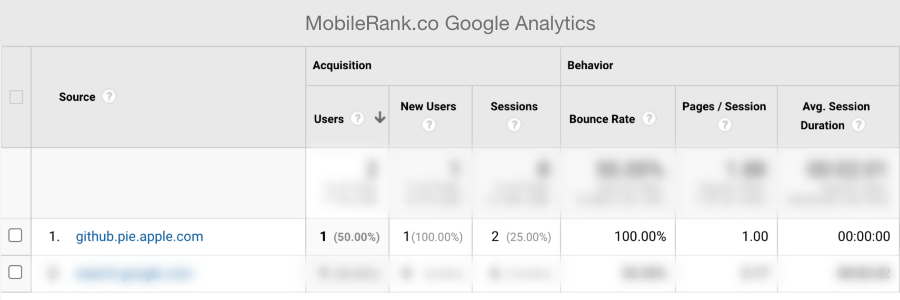
github.pie.apple.com or why you should configure referrer policy for internal company websites
Let’s start with a disclaimer that I have no knowledge if github.pie.apple.com is a legitimate domain belonging to Apple. If it does, it shows that Apple engineers are all in on Apple Pie puns.
How did I get to know about the github.pie.apple.com domain?
Every time you click on a HTML link the document.referrer property is set on the target website. This is how Google Analytics provides you with insights on which websites are linking to you and where your users are coming from.
My best guess is that someone clicked on a link leading to mobilerank.co from github.pie.apple.com and it showed up in my Google Analytics report.
The dangers of document.referrer for internal company websites
Knowing from where users get to your website is a very useful feature of the web. But when enabled on internal company websites can be quite dangerous.
The worst that can happen is if the referrer URL contains a session token. This would allow a malicious actor to hijack the session. This is the canonical example of the referrer URL attack.
Another risk comes from information disclosure. By giving away too much information, you are helping attackers to map your internal network. Knowing internal network layout and technologies used can make it easier to successfully launch other attacks.
How to avoid document.referrer from being set?
There are two main solutions which you can use to control what gets set to document.referrer property.
HTML rel attribute
You can stop browsers from setting document.referrer property by setting rel=”noreferrer” on HTML a tag. Read about other rel attribute options
<a href=”” rel=”noreferrer”>Awesome article</a>
Referrer-Policy HTTP header
Browser referrer behavior can also be controlled with HTTP headers by setting referrer-policy to no-referrer on the web server. This option is the preferred one since it does not require editing existing content and can be applied to the entire website. Read more about referrer-policy header
Referrer-Policy: no-referrer
Use automated security scanners
I admit that I have mixed feelings about automated security scanners. I have spent hours manually dismissing and writing explanations for security alerts which have no basis in reality. Nonetheless, security scanners would catch misconfigured or missing referrer policy and give you a signal that there might be an issue.